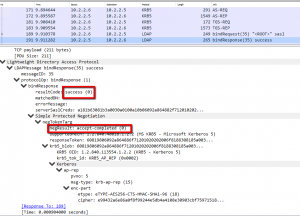
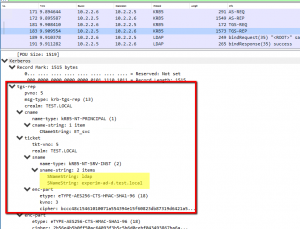
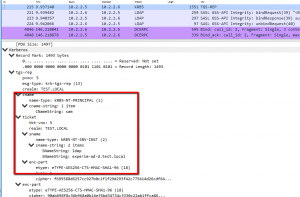
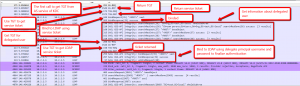
Here is a successful one.
[image: Inline image 1]
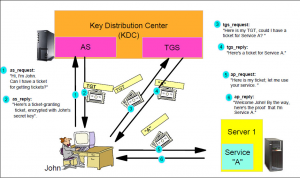
For a better understanding of each request, here is kerberos works.
diagram from: www.ibm.com/developerworks/ibmi/library/i-sso/index.html
[image: Inline image 2]
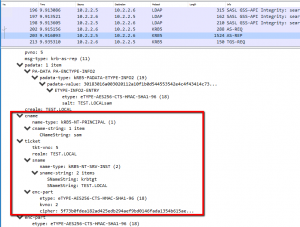
Here is how you verified if a TGT is returned.
[image: Inline image 3]
A Ticket is returned for LDAP for that user
[image: Inline image 4]
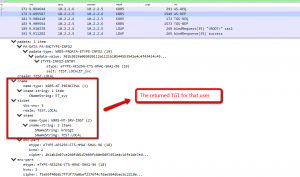
Main user bound.
[image: Inline image 5]
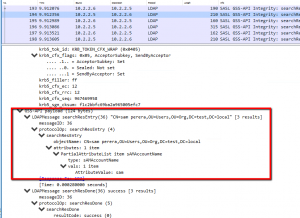
Infomation about delegated user back
[image: Inline image 6]
Got TGT for delegated User
[image: Inline image 7]
Get Ticket for delegated User
[image: Inline image 8]
Bind delegated user within SASL.
[image: Inline image 9]
Some code to read info of delegated user:
lkarolak.wordpress.com/2010/11/17/finding-active-directory-users-group-membership-in-c/